An easy way to get some traffic statistics of your router/ firewall/ switches and all the other stuff that supports snmp is the utility mrtg.
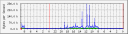
It helps you to find out quickly if more traffic than usual is passing your line. So you can interact fast if something suspicious is going on…
Whether your hardware supports snmp can be found out using the command:
snmpwalk -v 2c -c public 10.0.0.1 | less
-v = version (2c)
-c = community-password (public)
-ip = ip address of your hardware (10.0.0.1)
Don’t care too much about the output – it’s enough for the beginning if there is some at all…
1)
In the first step we’re generating a basic config (can be done by hand, but that’s rough work):
cfgmaker -global 'WorkDir: /srv/www/htdocs/mrtg' \
--output=/etc/mrtg.cfg public@10.0.0.1 public@10.0.0.2
WorkDir: output directory for the graphs
–output: target configuration file
public@10.0.0.1: first router
public@10.0.0.2: second router / switch / whatever
2)
With the following command you can create some basic web pages:
indexmaker -output=/srv/www/htdocs/mrtg/index.html \
-title="My Title" /etc/mrtg.cfg
-output: target index file
-title: title of the web page
/etc/mrtg.cfg: path to configuration file
3)
To get your statistics updated automatically, insert a cronjob like this:
*/5 * * * * env LANG=C /usr/bin/mrtg /etc/mrtg.cfg \
--logging=/var/log/mrtg.log
Category Archives: Security
exim / filtering spam
A graph to show you how many UCE-Mails are filtered per week.
This is a statistic from one of my company’s mailservers.
From about 3000 mails per hour -> more than 90% of all traffic is spam, UCE or virus-infected mail!
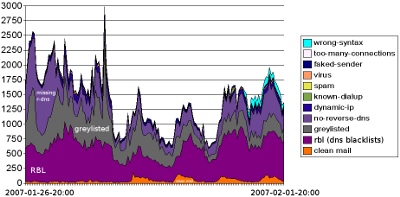
Explanation:
wrong-syntax: Somebody tried to fake a mail-programm
too-many-conn.: Anybody tried to send a mass-mail
faked-sender: Tried to spoof sender
virus: recognized virus (which was not blocked by other filters)
spam: recognized spam (which was not blocked by other filters)
known-dialup: known dialup notwork; normally no mail from here
dynamic ip: dialup network or forgot to set proper dns-reverse entry
no-reverse-dns: still allowed, but reverse dns should be set
greylisted: mail is rejected first time; after that it should be ok
rbl: dns blacklists
clean mail: passed through and should be ok
Astaro / Up2Date 7.001 released
A bugfix-only-release:
See: http://up2date.astaro.com/2007/01/up2date_7001_released_high.html
Astaro has fixed some issues like
– Up2date is not working
– Reporting does not work / does not generate graphs
– …
Update was installed without problems. A Restart wasn’t necessary.
First tryout of Astaro Firewall v.7.000
Yes, I know. It’s my own fault to use the first release of a software in a productive enviroment. But I just couldn’t wait.
Whatever, here are my first impressions:
- Installation went smooth, but I had to disconnect my second cd-rom-drive before I was able to finally finish the installation.
- The drag-and-drop gui is an nice idea, but I had some problems finding a browser to use it reasonable way.
- I had disconnects of almost every protocoll (ssh, rdp, ica) sporadically. Especially the VPN to my company was disturbed every 5 minutes so that I had to reconnect and reconnect ..
-> Solution was quite simple: I had to disable the IPS-system because a lot of packets were dropped wrongly. You also have to pay attention to the Peer2Peer and Instant-Messaging settings, because if any of these is active, IntrusionProtecion is activated automatically and might drop your packets ..
PS: Astaro Security Gateway can be used free for use at home.
Pimp my exim / DynaStop
I found a (new) software that finally helps to ban spam that is not blocked by various dns blacklists, greylisting, etc …
Have a look at:
http://tanaya.net/DynaStop/
and the forum:
http://www.exim-users.org/forums/forumdisplay.php?f=36
2007/05/08: Update of my personal DynaStop Whitelist
Here you’ll find a great piece of software, that filters incoming mail on the basis of whether a dynamic IP address is used. This reduces system load and resources in processing unwanted mail because all legitimate mail from mainly all ISPs will be sent from a proper mail exchange server (respectively the dns name). Over 350 million IP addresses were used in testing DynaStop for integrity and stability in identifying dynamic addresses and cross checked false positives.
Although the software is still in beta status, I use it in my company to kick out the rest of unwanted connections that are not recognized by RBLs or those that “survive” greylisting.
Result:
- System load is massive reduced because of less work for spamassassin and antivirus-software
- Connections that come back multiple times and overwit greylisting are banned without scanning the message
- Combined with a daily-report (to control false positives) of blocked networks it’s really a powerful software