Today I’ve implemented a new tool in our anti-spam system:
FuzzyOCR (Dec 13, 2007: URL contains ads only now)
It’s an OCR software used as a plugin for SpamAssassin.
OCR means “optical character recognition” and describes the procedure to recognize characters and words from images. It’s quite useful when you try to catch so-called “Image Spam”, which uses normal text where the real message is hidden in images (inline gifs, etc.)
The results are quite good and I’m confident : )
Additionally to the packages described on the homepage of FuzzyOCR you’ll need another piece of software (at least with openSuSE 10.0): giflib-progs-4.1.3-7.i586.rpm
Continue reading Pimp my spamassassin / FuzzyOCR
Monthly Archives: February 2007
Nagios 2.x Plugin check_mrtgtraf buggy?
affected:
…
nagios plugins 1.4.3
nagios plugins 1.4.5
nagios plugins 1.4.6 (Feb, 05 – 2007)
I was trying to implement the check_mrtgtraf plugin for nagios.
A test run in bash using the command
./check_mrtgtraf -F /my/mrtg/log/server.log -w "196608,196608" -c "235929,235929"
resulted in the following “error”:
Traffic UNKNOWN – Avg. In = 2.3 KB/s, Avg. Out = 2.3 KB/s ..
In my constellation the result should be “Traffic OK”, because the limit of 0,19 MByte/s (1,5 MBit) has not been reached. On http://archive.netbsd.se I found a hint from Israel Brewster that fixed it:
From: Israel Brewster
Date: 2007-01-26 17:54:06
—
I’m pretty sure this is a bug. I ran into the same thing, but was able to fix it easily enough in the source code. Looking at the original code for this plugin, you can find the section where it sets the output state, something like:
if (incoming_rate > incoming_critical_threshold
|| outgoing_rate >
outgoing_critical_threshold) {
result = STATE_CRITICAL;
}
else if (incoming_rate > incoming_warning_threshold
|| outgoing_rate >
outgoing_warning_threshold) {
result = STATE_WARNING;
}
This may not be exact, as I have modified the code somewhat, but I think it is pretty close, if not. At any rate, what you’ll notice is that while the result is set to STATE_CRITICAL or STATE_WARNING, depending on the circumstances, it is never set to STATE_OK (as you mentioned in your original message), which means that it remains in its STATE_UNKNOWN default state if the traffic is OK, to fix it, all you need to do is add the two lines:
else
result = STATE_OK;
Immediately following the closing bracket on the code block above, and recompile. At least, that fixed it for me. I have plugins version 1.4.3, I don’t know if this issue has been fixed in a newer version of the plugins or not (current is 1.4.5)
That workaround did it for me, too.
You can download my patched version of the c source right here: check_mrtgtraf.c – fixed version
ext2-support is lacking in openSuSE 10.2 kernel
Today, I was playing around with some Disaster Recovery software (Mondo Rescue and mkCDrec) and had to recognize after some tries and errors, that the created boot cdroms just didn’t work because SuSE removed the ext2-support from openSuSE 10.2 kernel. That’s really annoying, because the initrd filesystem cannot be mounted without it (in default configurations) and I did not get the minix fs to work yet ..
After some time spent searching on google, I found precompiled openSuSE 10.2 rpms at software.opensuse.org for Mondo Rescue.
But same problem for me -> backup worked like a charm but I still can’t boot from cdrom (hangs after a while).
I’ll try another Linux distribution next days and test that there, because the disaster recovery software seems to be very interesting and useful.
Do you like statistics?
An easy way to get some traffic statistics of your router/ firewall/ switches and all the other stuff that supports snmp is the utility mrtg.
It helps you to find out quickly if more traffic than usual is passing your line. So you can interact fast if something suspicious is going on…
Whether your hardware supports snmp can be found out using the command:
snmpwalk -v 2c -c public 10.0.0.1 | less
-v = version (2c)
-c = community-password (public)
-ip = ip address of your hardware (10.0.0.1)
Don’t care too much about the output – it’s enough for the beginning if there is some at all…
1)
In the first step we’re generating a basic config (can be done by hand, but that’s rough work):
cfgmaker -global 'WorkDir: /srv/www/htdocs/mrtg' \
--output=/etc/mrtg.cfg public@10.0.0.1 public@10.0.0.2
WorkDir: output directory for the graphs
–output: target configuration file
public@10.0.0.1: first router
public@10.0.0.2: second router / switch / whatever
2)
With the following command you can create some basic web pages:
indexmaker -output=/srv/www/htdocs/mrtg/index.html \
-title="My Title" /etc/mrtg.cfg
-output: target index file
-title: title of the web page
/etc/mrtg.cfg: path to configuration file
3)
To get your statistics updated automatically, insert a cronjob like this:
*/5 * * * * env LANG=C /usr/bin/mrtg /etc/mrtg.cfg \
--logging=/var/log/mrtg.log
Save and convert flash streams
If you want to convert a flash stream into a more comfortable format, that can be saved on your local disc and be played by most software/hardware, here’s a short guide:
Save your prefered video (from i.e. YouTube, MyVideo, etc.) with KeepVid.
When FFmpeg is installed, the conversion in Linux is quite simple:
ffmpeg -i input.flv -ab 128 -ar 44100 -b 900 \
-s 640x480 output.mpg
-b = videobitrate
-ab = audiobitrate
-ar = audiosamplerate (Hz)
-s = framesize width * height
exim / filtering spam
A graph to show you how many UCE-Mails are filtered per week.
This is a statistic from one of my company’s mailservers.
From about 3000 mails per hour -> more than 90% of all traffic is spam, UCE or virus-infected mail!
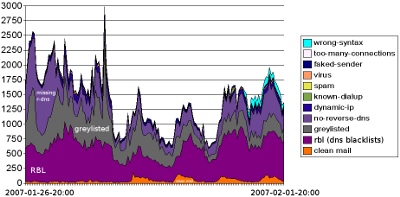
Explanation:
wrong-syntax: Somebody tried to fake a mail-programm
too-many-conn.: Anybody tried to send a mass-mail
faked-sender: Tried to spoof sender
virus: recognized virus (which was not blocked by other filters)
spam: recognized spam (which was not blocked by other filters)
known-dialup: known dialup notwork; normally no mail from here
dynamic ip: dialup network or forgot to set proper dns-reverse entry
no-reverse-dns: still allowed, but reverse dns should be set
greylisted: mail is rejected first time; after that it should be ok
rbl: dns blacklists
clean mail: passed through and should be ok
Joomla vs. WordPress
I get more and more requests for several special Apache settings, like: “please turn off Safe-Mode” regarding Joomla. I keep questioning myself what is the big advantage comparing Joomla to WordPress or any other CMS. Any suggestion is appreciated!